
Bitdefender Hypervisor Introspection
Eliminate Your Security Blind Spots

Bitdefender Hypervisor Introspection (HVI) CPU, 1 Year, 15-24 Users
*Price per license. Quantity must be 15 or greater.#2842ZZBSN120ALZZ
Get a Quote!
More info
Bitdefender Hypervisor Introspection(HVI), detects suspicious activities by working directly with raw memory – a level of insight from which malware cannot hide.
HVI is able to detect attacks that can be hidden in your infrastructure for days, weeks, or even months – spying and exfiltrating information invisibly.
HVI can also prevent further breaches, ensuring you have full visibility of the activity in your datacenter.
*Price per license. Quantity must be 15 or greater.
Get a Quote!
Click here to jump to more pricing!
Overview:
What secrets does your infrastructure hold?
In late 2013, a standard investigation on a bank in Kiev revealed that for several months the internal systems were being monitored by stealth malware. The malicious software was highly successful at covering its tracks, recording every employee’s move, and even sending back video feeds and images, all without raising suspicion.1
When finally discovered, the sophisticated attack - known today as Carbanak - was eventually linked to more than one-hundred banks across thirty nations, revealing one of the largest bank thefts ever. This attack inflicted an estimated $1 billion worth of damage globally.2
Carbanak is just one of a series of targeted attacks that breached data in key industries around the world, by using stealth malware to gain entrance while avoiding detection. While there are many other similar examples of attacks, no proactive technology has yet been proven effective enough to single out these deep threats.
How malware out-privileges you, without you knowing it
Operating systems were not designed with security in-mind. Malicious code is able to run with kernel privilege, just like your security solution, and stands a good chance of bypassing your security.
After it surreptitiously infiltrates the system, both the workloads and the system remain operable. While everything may seem fine, it is only a front for data exfiltration and cyber-espionage.
Some malware can even brings an infrastructure to its knees
The damage inflicted by successful attacks on a system increases with the time to mitigate. Even a relatively innocuous malware, such a spam-sending Trojan, will impact the resources of an organization. Ultimately, it can impact profit by consuming resources, which may even be partly directed at employees of the company itself, inflicting further wasted time on the company.
5 months pass before an infiltration is uncovered
A study conducted in February 2016 shows it takes companies an average of 5 months to detect a data breach. What’s more, 53% of them needed external investigators to discover them, as internal resources showed no signs of a breach.3
Bitdefender and Citrix Join Forces to Root out Deep Threats from Your Infrastructure
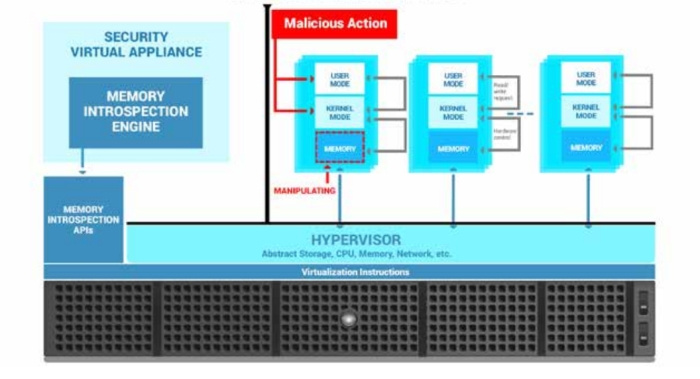
By joining their considerable expertise in IT security and data center virtualization, Bitdefender and Citrix have developed an entirely new security layer which malware cannot compromise or evade – through raw memory introspection directly at the hypervisor level.
How do you catch that which you cannot see?
If a rootkit or kernel exploit tricked the operating system into hiding its tracks, even advanced security solutions will have difficulties discovering them, if those security solutions are in-guest. The trick is viewing a VM from the outside, while also monitoring its inside processes. The approach lies within the bare-metal hypervisor – a tool that hasn’t been used for security before. They hypervisor provides the context of VMs, while staying isolated from them. In an unprecedented collaboration against targeted attacks, Bitdefender and Citrix put their collective expertize in virtualization and security on the table. Together, they created a new security layer that will see everything happening in your infrastructure, but which malware cannot reach.
A solution deemed impossible to achieve
The way to catch the most advanced threats is to not rely on information given to you by the OS. Hypervisors provide clean, low-level information about the memory being used by each virtual machine. To provide these insights, Citrix is now introducing a new, specially designed API in XenServer, which offers insight into the raw memory stack of every virtual machine from the hypervisor. At this level, access to memory is so raw, and at such a low-level, that analyzing it has been impossible so far -- only a handful of people in the world write security at this level. Bitdefender is now introducing Hypervisor Introspection(HVI), a ground-breaking solution that detects suspicious activities by working directly with raw memory – a level of insight from which malware cannot hide.
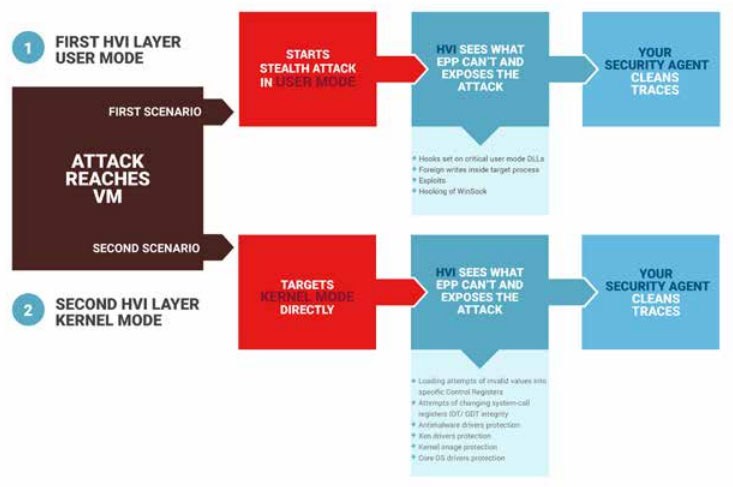
An innovative security layer that protects your privileges
Working together, Bitdefender and Citrix are now giving datacenter owners the ability to know the previously unknowable, and act on information from this new level of insight.
Bitdefender Hypervisor Introspection (HVI)
HVI is able to detect attacks that can be hidden in your infrastructure for days, weeks, or even months – spying and exfiltrating information invisibly. HVI does not assume your systems are clean upon arrival; you can instruct HVI to inject cleaning tools into live virtual machines – a temporary footprint into running systems. This also allows your native endpoint protection to take care of the rest, from within the VM. HVI can also prevent further breaches, ensuring you have full visibility of the activity in your datacenter.
Already proven against targeted attacks
HVI already detects and blocks famous targeted attacks including Carbanak, Turla, APT28, NetTraveler or Wild Neutron without knowing beforehand the actual vulnerabilities used by the hackers.
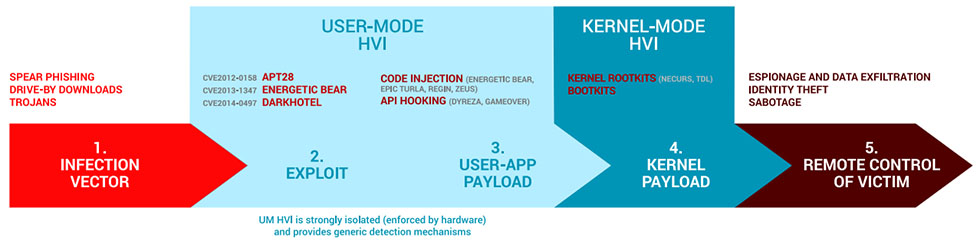
Among the targeted attacks that HVI can detect is a massive cyber-espionage campaign uncovered in 2015 by Bitdefender called APT28. The attackers infiltrated political, e-crime services, telecommunication services or aerospace industries in US and Eastern Europe – stealing passwords, and gaining system privileges – all while remaining undetected. Coincidentally, during this period, in Minsk, the political leaders of Belarus, Russia, Germany, France and Ukraine were participating in a summit, discussing the ceasefire in the Donbass region in the east of Ukraine.4
Minimum Investment. Easy to Deploy.
Unlike other vendors that require you to remove your endpoint protection and replace it with theirs, HVI is complementary to your existing security tools. It is a new security layer, and is fully compatible with every existing EPP today. It also works hand in-hand with you current agent-based solution – it stops attackers from gaining privileges on your infrastructure, preventing them from hiding from your in-guest security.
1 http://www.nytimes.com/2015/02/15/world/bank-hackers-steal-millions-via-malware.html
2 https://threatpost.com/carbanak-ring-steals-1-billion-from-banks/111054/
3 https://www2.fireeye.com/rs/848-DID-242/images/Mtrends2016.pdf
4 http://download.bitdefender.com/resources/media/materials/white-papers/en/Bitdefender_In-depth_analysis_of_APT28–The_Political_Cyber-Espionage.pdf
Benefits:
A revolutionary security layer. Malware cannot reach it, and cannot hide from it.
Raw Memory Introspection - They said it was impossible
Bitdefender Hypervisor Introspection (HVI) is the first security solution that is able to uncover memory violations that endpoint security tools sometimes miss by directly analyzing raw memory lines - thereby ensuring they are not being altered by malware.
Isolated and impossible to compromise, even by Kernel-Level Malware
Positioned completely outside the operating system, with hardware-enforced isolation, and with no agent or drivers installed on the endpoints, Bitdefender Hypervisor Introspection is impossible to take down or compromise by rootkits or other kernel-level threats.
Detects zero-days that heuristics miss
By focusing on techniques, rather than the payloads, Bitdefender HVI is able to stay ahead of attacks, and protect you against notorious attack gateways such as browser zero-days or spear-phishing emails with exploited files attached that are not visible from within the guest OS.
Eliminate your security blind spots
Respond instantly to attacks
Apart from containing the attack in real time, Bitdefender HVI can also help remove the threat, by automatically injecting a temporary remediation tool in the affected Virtual Machine.
Learn of ongoing attacks in real time and see the attack chain
Bitdefender HVI sends out alerts the instant a memory violation is detected, and provides detailed reporting of the attack chain, including affected processes, type of violation, and timeline of the attack.
Independent from and fully compatible with every endpoint security tool
Instead of inserting an agent into each VM, Bitdefender HVI detects and secures infrastructures directly at hypervisor level, through a security virtual appliance. This is why, unlike other vendors that require you to remove your endpoint protection and replace it with theirs, Bitdefender HVI is complementary to and compatible with any existing security tools.
Fast Deployment. Easy to Manage. High Performance.
Agentless security - fast to deploy and easy to manage
Bitdefender HVI’s centralized approach to security makes its deployment a matter of minutes and its management straightforward, through Bitdefender’s GravityZone Control Center.
Optimized for performance - brings little to no impact on consolidation ratios.
After much invested effort, Bitdefender HVI now monitors your infrastructure
without impacting consolidation ratios, or slowing down user activity on the VM.
System Requirements:
Supported Guest Operating Systems
Windows desktop operating systems:
- Windows 7
- Windows 8
- Windows 8.1
- Windows 10
Windows server operating systems:
- Windows Server 2008 R2
- Windows Server 2012
- Windows Server 2012 R2
- Windows Server 2016
Linux operating systems:
- Debian 8, 64-bit
- Ubuntu 16.04 LTS, 64-bit
- Ubuntu 14.04 LTS 64-bit
- CentOS 7, 64-bit
- Red Hat Enterprise
Host Requirements
CPU microarchitecture:
- Any Intel® Sandy Bridge processor or later, with support for Intel® Virtualization Technology.
- VT-x or VT-d extensions must be enabled in BIOS.
Software requirement:
- requires XenServer 7.x to run
Video:
HVI Defeats EternalBlue (associated to WannaCry):
Demo of Secure Browsing With Bitdefender HVI & XenApp
Documentation:
Download the Bitdefender Hypervisor Introspection Datasheet (.PDF)
Pricing Notes:
- Pricing and product availability subject to change without notice.
*Price per license. Quantity must be 15 or greater.
Get a Quote!
*Price per license. Quantity must be 25 or greater.
Get a Quote!
*Price per license. Quantity must be 1 or greater.
Get a Quote!
*Price per license. Quantity must be 50 or greater.
Get a Quote!
*Price per license. Quantity must be 100 or greater.
Get a Quote!
*Price per license. Quantity must be 1 or greater.
Get a Quote!
*Price per license. Quantity must be 15 or greater.
Get a Quote!
*Price per license. Quantity must be 25 or greater.
Get a Quote!
*Price per license. Quantity must be 50 or greater.
Get a Quote!
*Price per license. Quantity must be 100 or greater.
Get a Quote!
*Price per license. Quantity must be 1 or greater.
Get a Quote!
*Price per license. Quantity must be 15 or greater.
Get a Quote!
*Price per license. Quantity must be 25 or greater.
Get a Quote!
*Price per license. Quantity must be 50 or greater.
Get a Quote!

